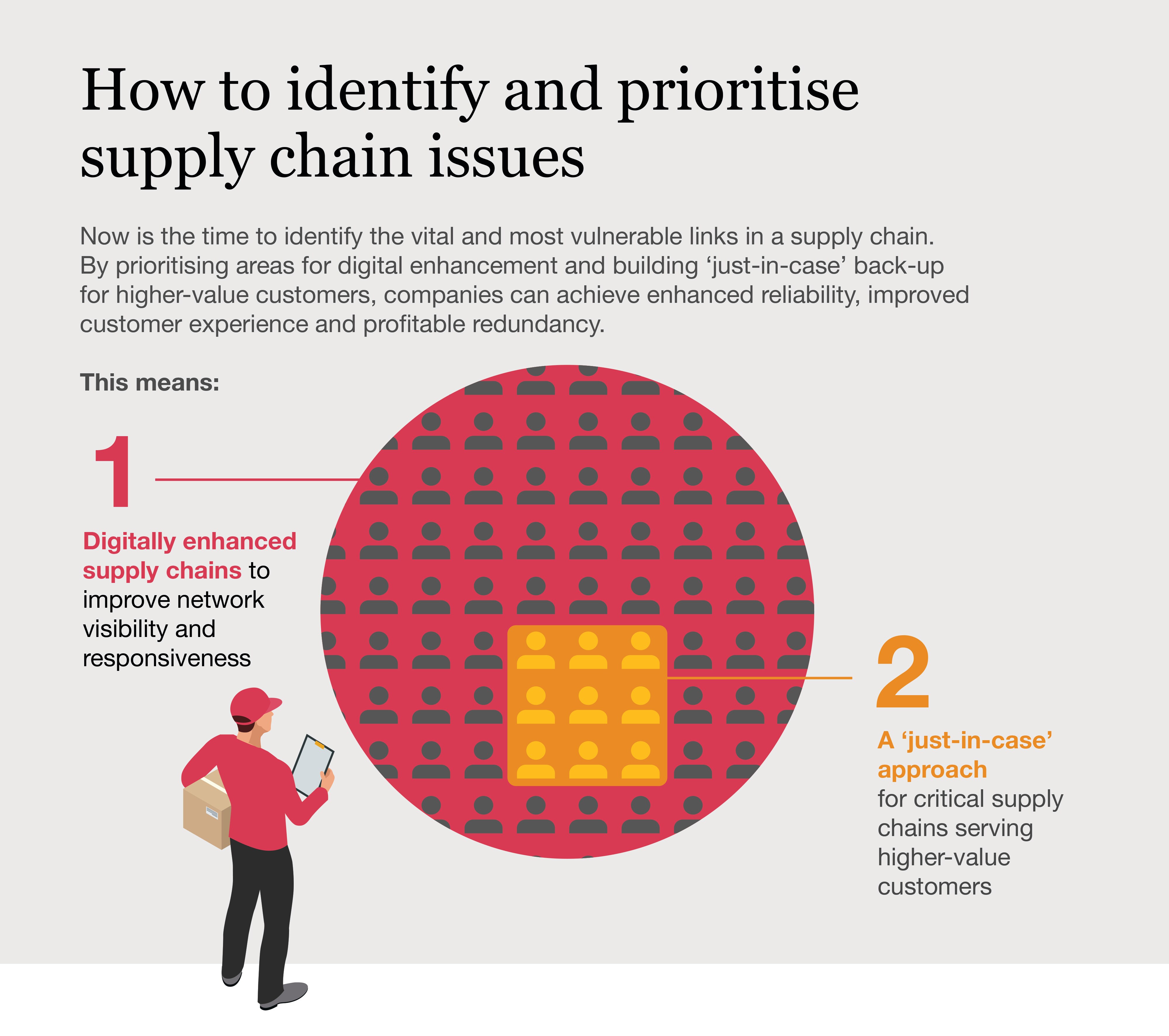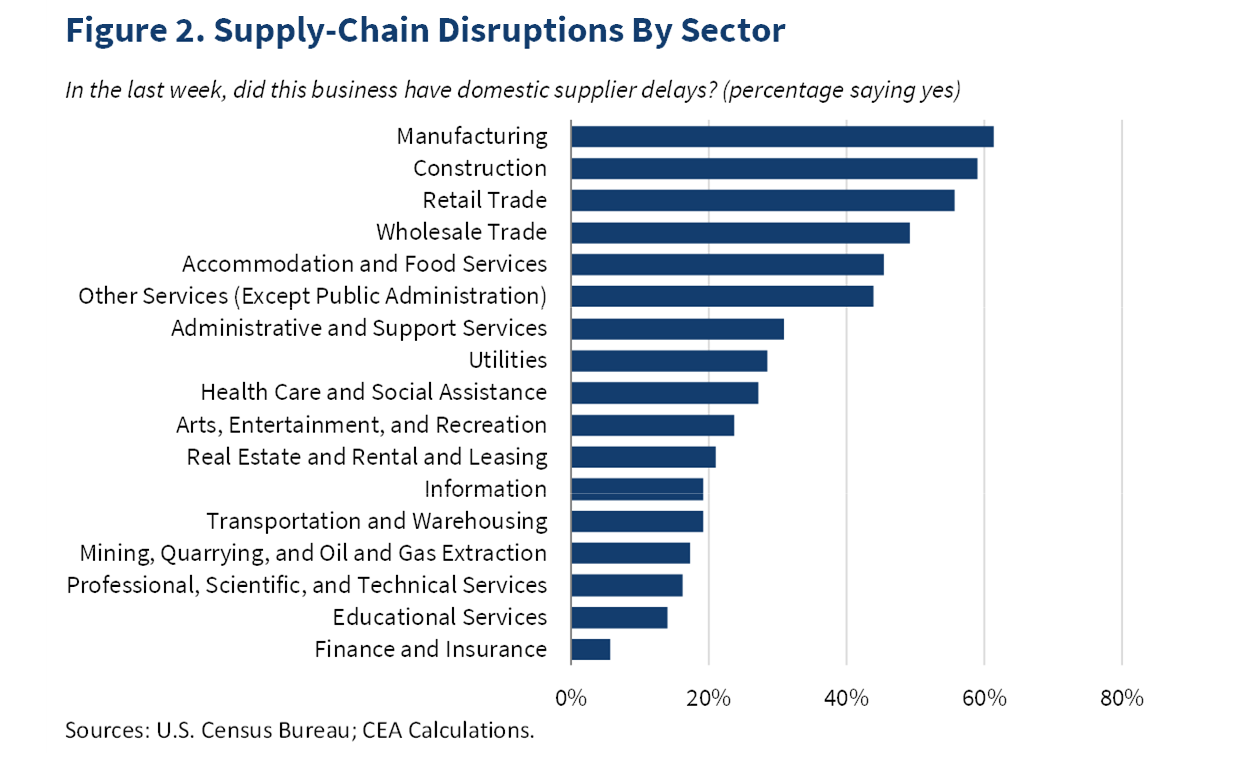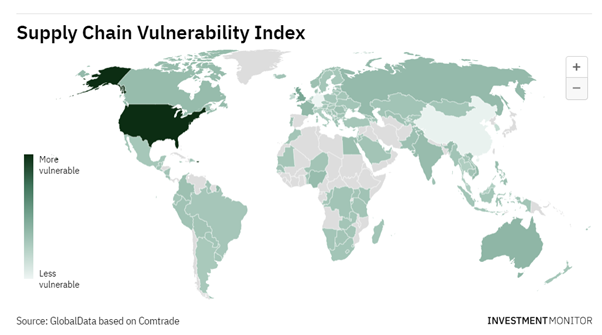
4 August Update: Future of supply chain, Developing Countries Trading Scheme, EV reimbursement tax shambles, FDI by country, Lithuania FDI, - Trade Horizons

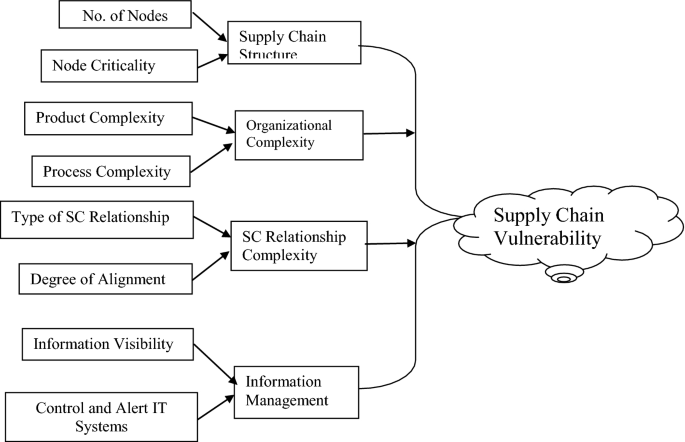
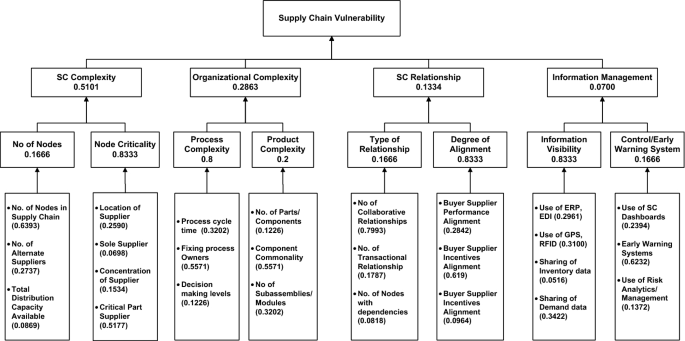
Spectrum of supply chain vulnerabilities: examples of potential disruptions | Download Scientific Diagram